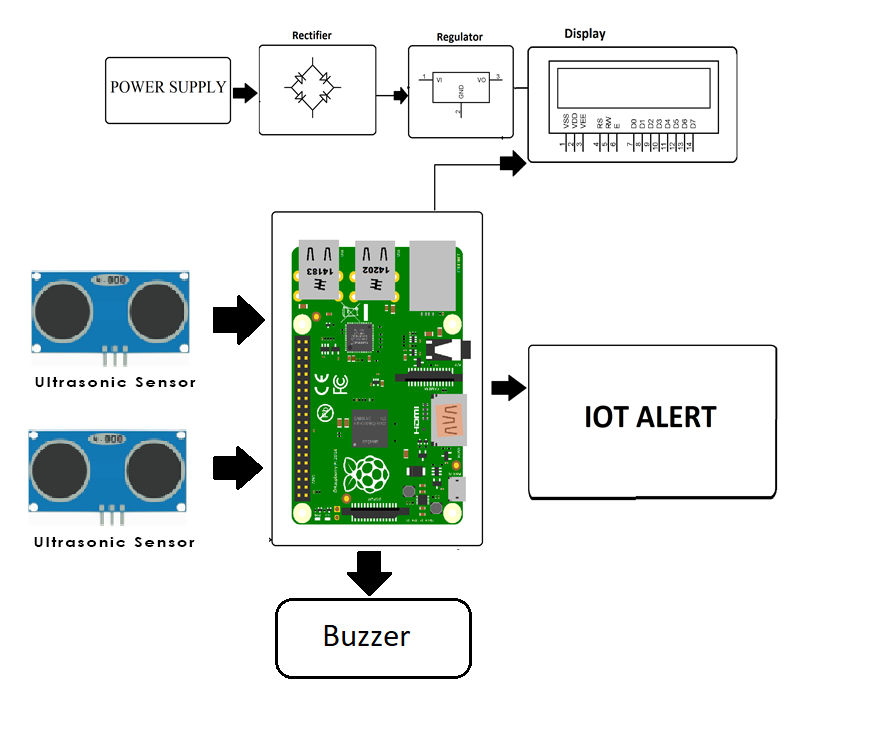
Mastering Remote IoT Monitoring With Raspberry Pi And SSH
Remote IoT monitoring through SSH is rapidly gaining traction as businesses and individuals seek efficient ways to manage their connected devices. With the proliferation of the Internet of Things (IoT), the ability to manage devices remotely has become indispensable. By integrating tools like Raspberry Pi and SSH, users can achieve comprehensive control over their IoT ecosystems, even when miles apart.
In today's interconnected world, IoT technology has transformed how we interact with everyday devices, enabling remote monitoring and management. This capability is particularly vital for industries such as agriculture, manufacturing, and healthcare, where real-time data is indispensable. Remote IoT monitoring empowers users to securely access and manage their devices, ensuring seamless operations and minimizing downtime.
Raspberry Pi stands out as an exceptional choice for centralizing remote IoT monitoring due to its affordability, adaptability, and user-friendly nature. When paired with SSH (Secure Shell), Raspberry Pi delivers a secure and dependable method for managing IoT devices from any location. This article will delve into how to download and configure Raspberry Pi for remote IoT monitoring via SSH, complete with detailed instructions and expert advice.
Read also:Alexis Bellino Net Worth 2023 A Deep Dive Into Her Wealth Career And Lifestyle
Table of Contents
- Introduction to Remote IoT Monitoring
- Understanding SSH
- Why Raspberry Pi?
- Installation Process
- Securing Your SSH Connection
- Downloading Raspberry Pi OS
- Setting Up Remote Monitoring
- Troubleshooting Common Issues
- Advanced Features
- Conclusion
Exploring Remote IoT Monitoring
Remote IoT monitoring leverages cutting-edge technologies to observe and manage IoT devices from afar. This practice is pivotal for maintaining system efficiency and ensuring that all devices operate at peak performance. Whether you're tracking environmental sensors, overseeing industrial machinery, or automating your home systems, remote IoT monitoring equips you with the tools to stay informed and in control.
Core Advantages of Remote IoT Monitoring
- Enhanced system reliability through real-time data analysis and actionable insights.
- Substantial cost savings by reducing the necessity for on-site visits and manual intervention.
- Fortified security through continuous monitoring, automated alerts, and proactive threat detection.
- Scalability to accommodate the expansion of IoT networks as your requirements grow.
With the escalating demand for remote access solutions, SSH and Raspberry Pi have emerged as leading contenders for establishing secure and efficient IoT monitoring frameworks.
Delving into SSH
SSH (Secure Shell) is a robust network protocol that enables users to securely access and manage remote devices over potentially insecure networks. It employs encryption for all data transmitted between the client and server, ensuring that sensitive information remains safeguarded from unauthorized access.
Why Opt for SSH in Remote IoT Monitoring?
- SSH delivers robust encryption, making it an ideal choice for securing IoT connections against potential threats.
- It supports command-line access, empowering users to execute commands remotely with precision and flexibility.
- SSH is highly configurable and can seamlessly integrate with firewalls and other network security measures to enhance overall system security.
By incorporating SSH into your IoT infrastructure, you can ensure that your devices remain accessible exclusively to authorized users, significantly mitigating the risks of cyberattacks and data breaches.
The Role of Raspberry Pi in IoT
Raspberry Pi is a compact, cost-effective single-board computer that has captivated hobbyists, developers, and professionals alike. Its diminutive size, impressive performance, and extensive community support render it an outstanding choice for remote IoT monitoring projects.
Benefits of Utilizing Raspberry Pi for IoT
- An economical solution for constructing IoT systems without compromising on quality or functionality.
- Supports a diverse range of operating systems, including the versatile Raspberry Pi OS, tailored for various applications.
- Highly compatible with numerous sensors and hardware components, expanding its versatility and application scope.
- Programmable and customizable to suit specific project requirements, empowering users to tailor solutions to their unique needs.
Raspberry Pi natively supports SSH, simplifying the process of setting up remote access for your IoT devices and streamlining the overall configuration process.
Read also:Discovering The Most Dangerous Zodiac Sign When Angry Unveiling Astrological Insights
Navigating the Installation Process
Configuring Raspberry Pi for remote IoT monitoring via SSH involves multiple stages, ranging from downloading the operating system to fine-tuning network settings. Below is a detailed guide to assist you in initiating this setup:
Step 1: Acquiring Raspberry Pi OS
Commence by downloading the latest iteration of Raspberry Pi OS from the official website. Select the version that aligns with your project specifications, such as the comprehensive desktop edition or the streamlined lightweight variant without a graphical interface.
Step 2: Writing the OS to an SD Card
Leverage tools like BalenaEtcher or Raspberry Pi Imager to write the downloaded OS image onto an SD card. Ensure the SD card is properly formatted and possesses adequate storage capacity to accommodate your project requirements.
Step 3: Activating SSH
To enable SSH on your Raspberry Pi, create an empty file named "ssh" (without an extension) in the boot partition of the SD card. This action will activate SSH functionality during the initial boot sequence.
Fortifying Your SSH Connection
Although SSH inherently provides a secure connection, additional measures can further enhance its security profile:
1. Implementing Strong Passwords
Establish a strong, unique password for your Raspberry Pi user account. Avoid utilizing common or predictable passwords that could compromise system security.
2. Disabling Root Login
Prevent unauthorized users from gaining administrative access by disabling root login. This can be achieved by modifying the SSH configuration file located at /etc/ssh/sshd_config.
3. Adopting Key-Based Authentication
Instead of relying on passwords, consider implementing key-based authentication for SSH. This method involves generating a public/private key pair and configuring your Raspberry Pi to authenticate connections solely through the private key.
Procuring Raspberry Pi OS
Raspberry Pi OS serves as the official operating system for Raspberry Pi devices, offering an extensive array of features and tools tailored for developers and enthusiasts. To download Raspberry Pi OS, adhere to the following steps:
Step 1: Accessing the Official Website
Visit the Raspberry Pi official website and navigate to the "Downloads" section. From there, select the appropriate version of Raspberry Pi OS that aligns with your project objectives.
Step 2: Selecting the Suitable Version
Raspberry Pi OS is available in three distinct variants: Desktop, Desktop with Recommended Software, and Lite. The Lite version is particularly suited for headless setups, such as remote IoT monitoring, as it excludes a graphical interface to enhance performance and efficiency.
Step 3: Verifying the Download
After downloading the OS image, verify its authenticity by comparing the checksum provided on the website with the checksum of the downloaded file. This step ensures the file has not been tampered with during the download process.
Configuring Remote Monitoring
Once your Raspberry Pi is equipped with SSH, you can proceed to establish your remote IoT monitoring system. This process encompasses connecting sensors, configuring data collection mechanisms, and securing a connection to your Raspberry Pi.
1. Connecting Sensors
Attach the necessary sensors to your Raspberry Pi, such as temperature, humidity, or motion detectors. Ensure all sensors are correctly wired and adequately powered to function optimally.
2. Configuring Data Collection
Develop a script or utilize a pre-built application to gather data from the sensors and store it in a database or file. Tools like Python or Node-RED can simplify this process, offering user-friendly interfaces and extensive documentation.
3. Accessing Data Remotely
Employ SSH to connect to your Raspberry Pi from a remote location and retrieve the accumulated data. Additionally, you can set up a web server to display the data in real-time, rendering it accessible through any standard web browser.
Addressing Common Issues
When establishing remote IoT monitoring with Raspberry Pi and SSH, you may encounter certain common challenges. Below are strategies to resolve these issues effectively:
1. SSH Connection Refused
If you encounter an "SSH connection refused" error, confirm that SSH is enabled on your Raspberry Pi and that the correct IP address is being utilized. Examine the firewall settings to ensure port 22 (the default SSH port) is open and accessible.
2. Slow Data Transfer
If data transfer speeds are sluggish, consider optimizing your network configuration or upgrading your internet connection. Compressing data before transmission can also reduce bandwidth consumption and enhance transfer efficiency.
3. Sensor Connectivity Problems
Verify that all sensors are properly connected and powered. Test each sensor individually to pinpoint any faulty components or wiring issues that may impede functionality.
Exploring Advanced Features
As you gain familiarity with remote IoT monitoring using Raspberry Pi and SSH, you can investigate advanced features to augment your system's capabilities:
1. Automation
Establish automation scripts to handle routine tasks, such as data backups and system updates, eliminating the need for manual intervention and conserving valuable time and resources.
2. Machine Learning Integration
Incorporate machine learning algorithms to analyze sensor data and predict potential issues proactively. This approach can significantly enhance system reliability and operational efficiency, offering actionable insights to address challenges before they escalate.
3. Cloud Connectivity
Link your Raspberry Pi to cloud platforms like AWS IoT or Google Cloud IoT Core to unlock advanced data analytics and visualization capabilities, enabling deeper insights and more informed decision-making.
Final Thoughts
Remote IoT monitoring via SSH using Raspberry Pi presents a powerful and adaptable solution for managing connected devices globally. By following the steps outlined in this article, you can establish a secure and efficient system tailored to your unique needs.
We encourage you to explore the advanced features discussed to further refine and expand your IoT setup. Share your experiences and insights in the comments section below, and for additional resources on Raspberry Pi and IoT, explore our other articles and guides.